Fortifying the Enterprise: Our Scalable, Dual-Mode API Key Rotation Engine
Authors - Rudra Deshpande, Chendra Namuri, Brian Hanks
In today's interconnected digital ecosystem, APIs are the lifeblood of modern applications, powering everything from internal microservices to external partner integrations. At our scale, managing security for hundreds of internal applications and over 280 external vendors is a monumental task. One of the most critical aspects of API security is the regular rotation of API keys. Manual key rotation is not only cumbersome and prone to human error but also a significant security risk, especially in a large and diverse ecosystem.
At our core, we are committed to innovation. Our platform delivers continuous, policy-driven API key governance for hundreds of internal applications and 280+ external vendor integrations. Unlike conventional point utilities that simply expose a rotation endpoint, we provide an end-to-end adoption framework, automated orchestration, flexible manual fallback, multi-environment tooling, and governed observability—designed for secure scale.
The Challenge: API Key Management at Scale
Traditionally, managing API keys is a manual process, fraught with challenges that are magnified at enterprise scale:
- Security Vulnerabilities – Stale, long-lived API keys are a prime target for attackers.
- Operational Overhead – Tracking, rotating, and updating keys across hundreds of applications consumes significant engineering time.
- Inconsistent Policy Enforcement – Ensuring that 280+ external vendors adhere to rotation SLAs is impractical with manual processes.
- Human Error Risks – Manual operations introduce outages and integration drift.
- Scalability Limits – Growth amplifies inconsistency and credential sprawl.
The Result: These pain points create a widening gap between security mandates and operational capacity—unless rotation becomes a governed, automated control plane.
Our Solution: A Paradigm Shift
We engineered a dual mode API key rotation platform that abstracts complexity away from consumers. Where the industry typically stops at “here is an endpoint—build your own scheduler,” we supply a packaged suite that secures the entire lifecycle:
- Discovery
Identify all active API keys, their owners, and associated applications. - Notification & Planning
Inform stakeholders of upcoming key renewal, provide timelines, and prepare for the transition. - Key Generation
Create new API keys using secure processes, ensuring proper permissions and metadata tagging. - Distribution
Securely delivers new keys to consumers (internal teams or external vendors). - Integration & Validation
Consumers update their integrations to use the new keys and validate functionality using our automated or manual key renewal options. - Monitoring
Comprehensive Dashboard to track usage of new and old keys, monitor for errors or anomalies, and ensure smooth operation. - Revocation
Deactivate or revoke old keys post key expiry date, closing the security window. - Audit & Reporting
Log all renewal activities, review compliance, and generate reports for governance.
Our API Key Rotation solution offers Dual Adoption Modes for Maximum Flexibility
- Fully Automated Rotation – Effortless, secure API key rotation with zero coding.
- On-Demand Manual Rotation – Portal-driven for regulated change windows or targeted forensic actions.
Differentiation vs Industry Norms
| Challenge | Typical Industry Approach | Our Platform Advantage |
|---|---|---|
| Security | Generic checks lacking location sensitivity | Location-Bound Key Rotator, once initialized with a unique fingerprint, it works only from that location. |
| Adoption Friction | Requires manual code changes per application | Zero-code onboarding using our fully automated solution. |
| Vendor Diversity | Tied to a single environment or vendor | Multi-environmental Key rotation support for seamless portability. |
| Policy Consistency | Reliant on manual documentation & audits | Automated policy enforcement with defined age windows & real-time metrics. |
| Rollback | Manual recreation of previous state | One-click reactivation with our automated governance solution. |
| Observability | Disparate, unstructured logs | Structured events with compliance-grade signals. |
| Future Expansion | Requires rebuilding integrations | Plug-in adapter model for rapid feature extension. |
Key Benefits (Outcome Focused)
- Enhanced Security – Shorter key lifetimes reduce exposure and strengthen overall security posture.
- Operational Efficiency – Automation frees engineering effort from repetitive manual refresh tasks.
- Flexible Adoption – Auto-enabled by default with controlled manual fallback for smooth integration.
- Reduced Downtime Risk – Conditional, idempotent updates prevent unnecessary secret churn.
- Scalable Consistency – Uniform key management across all internal and external systems.
Operational Outcomes
| Metric | Before | Now |
|---|---|---|
| Manual Tickets / Month | Dozens of requests & escalations | Near-zero — automated handling. |
| Blast Radius | Multi-application chain risk | Isolated impact via short key lifespan. |
| Key Expiry Compliance | Often missed, causing service disruptions | Fully automated renewal ensures 100% compliance. |
| Key rotation effort | Hours to days per Company/Apps | Seconds to minutes via Key Rotation automation. |
| Operation Overhead | High due to repetitive tasks | Minimal, with streamlined, policy-driven automation. |
Our Automated Solution:
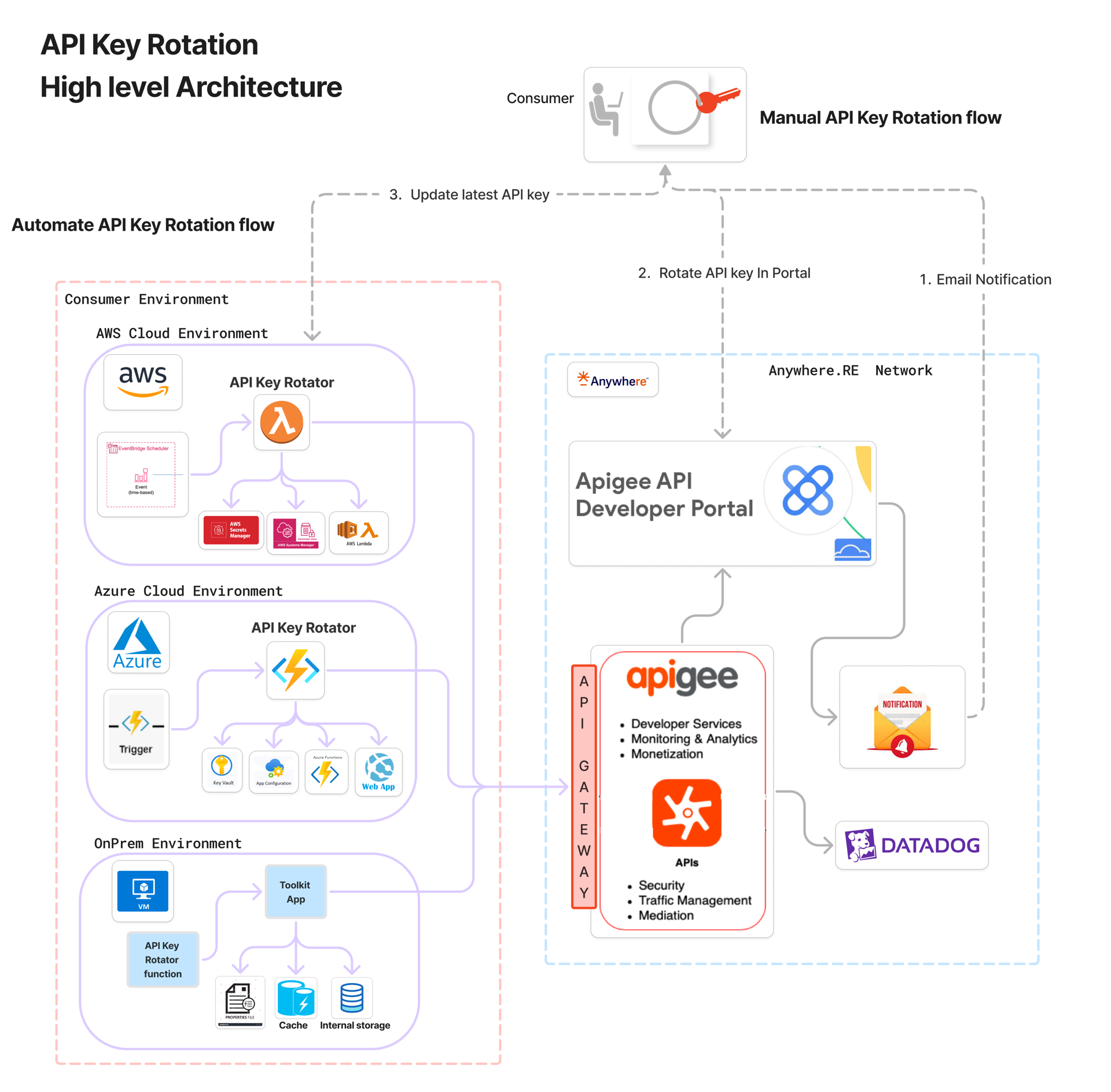
Our delivery model meets applications where they run—no refactor required. We support cloud-native, hybrid, and on-prem environments
| Platform | Toolkit Offering | Key Capabilities |
|---|---|---|
| AWS Native | Toolkit Lambda Extension + API Key Rotator template | Rotate keys in Secrets Manager, SSM Parameter Store, Lambda environment variables. |
| Azure Native | Azure API Key Rotator Function template | Rotate keys in Azure Key Vault, App Configuration, Function App environment variables, WebApp, Static WebApp. |
| On-Prem (Windows / Linux / Mac) | Standalone Toolkit | Manage property files / host-managed keys. |
This multiplatform approach eliminates refactor friction and accelerates secure onboarding.
Security & Governance – Condensed
- Least Privilege – Scoped Access Only:
API keys are scoped to specific applications and environments; no wildcard permissions exist beyond their declared scope.
- Encrypted Everywhere – Secure Key Storage :
All API keys and sensitive company configuration remain encrypted at all times during generation, storage, and rotation.
- Tamper Guardrails – Prevent Unauthorized Reuse :
Quickly disable or invalidate API keys if suspicious activity is detected.
- Policy Enforcement – Continuous Compliance Monitoring:
Rotation schedules, key lifetimes, and compliance rules are monitored; deviations are promptly addressed.
- Audit Evidence – Structured, tamper-proof logs simplify compliance:
All key generation, rotation, distribution, and revocation events are logged with structured, tamper-evident records for governance and compliance.
The Future is Secure, Flexible, and Automated
Proactive, automated credential governance is no longer optional in modern threat landscapes. Our dual‑mode platform transforms rotation from a periodic chore into a continuous assurance mechanism—empowering teams to innovate confidently.
To learn more, explore our API Key Rotation User Guide (https://developers.anywhere.re/blog/api-key-rotation-user-guide) or engage via the developer portal for advanced onboarding and roadmap collaboration.
